SSL/TLS certificates are one of the methods we use to secure and verify communication on today’s internet. While SSL-secured HTTPS versus unsecured HTTP doesn’t seem much different than it has been for the past few decades, a lot has been going on in the technology industry to get SSL pushed out to more devices in a more secure way. In this post, we’ll examine how SSL has been used in the past and how it’s adapting to the ways we’re using it in today’s environment.
History: SSL in the Past
For years, we’ve been told to look for the green lock in the URL bar to tell us when we are browsing a secure website. This green lock and the “S” in HTTPS indicates that the website is secured with an SSL/TLS certificate (Secure Socket Layer or Transport Layer Security certificate). Not only does SSL encrypt your session with that website, but it also helps to validate the identity of the website. In this example, you can be assured that this website is actually owned by AVENDE.COM and not some third-party site masquerading as AVENDE.COM.
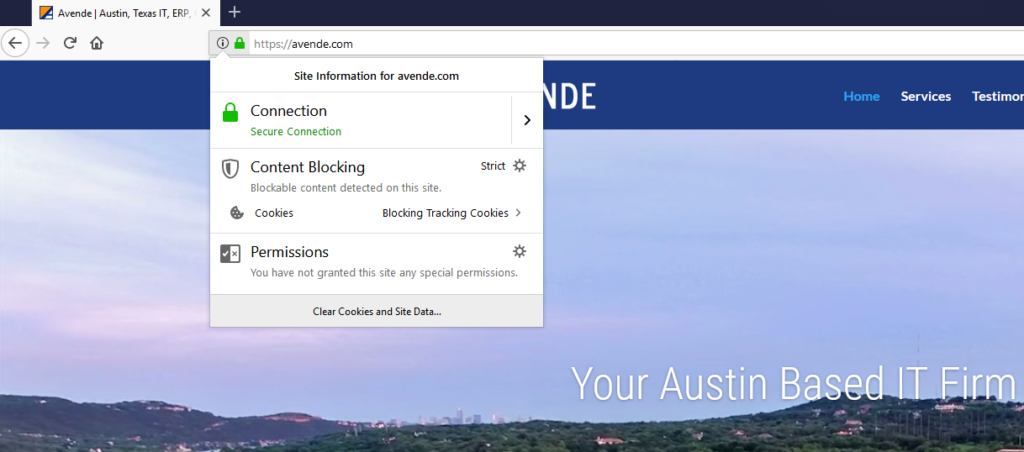
SSL works because everybody’s computer, phone, web browser, or other internet-connected device keeps a list of trusted certificate authorities (CAs) that they will trust to sign-off on certificates for other sites. When your company needs a certificate to secure your website, you would reach out to a certificate authority like Comodo®, GoDaddy®, or DigiCert® (Formerly Symantec/Verisign), who would charge $50 or more (and sometimes much, much more depending on the type of certificate) to verify ownership of your domain name. Once they verify domain ownership, the CA would issue you a certificate that would typically be good for 1-3 years.
Problems: Cost and Vulnerabilities
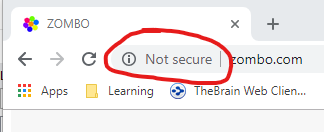
In recent years, there has been a push to secure the web. SSL is no longer just recommended for banking websites and shopping carts – the industry has been pushing for HTTPS everywhere, even for small business sites that don’t take credit card information or even personal websites. Some browsers, such as Google Chrome, will show “Not secure” in the URL bar if you browse to an insecure HTTP site.
In addition, SSL/TLS certificates aren’t just for the web – TLS is often used to secure other previously unsecured services, such as SMTP (email), or is used to replace other encryption methods that have their own faults (SSL-secured SSTP VPNs are replacing many PPTP and L2TP VPNs).
This push has created more scrutiny of our SSL and TLS security protocols. In the past, during the lifetime of a certificate, you may only need to revoke and re-issue it once or twice because of a patched vulnerability, but nowadays it seems that a new vulnerability pops up every few months. Some have even made national news – you may have heard about vulnerabilities such as BEAST, SUPERFISH, DROWN, POODLE, or HEARTBLEED.
The Future: SSL/TLS Going Forward
While you may still purchase certificates from the same old CAs (and sometimes may need to, depending on your certificate requirements), one cheaper and easier option has arisen in recent years.

The Internet Security Research Group™ has developed Let’s Encrypt™, a service that provides free certificates to anybody who wants one. The catch is that Let’s Encrypt certificates are only good for 90 days. This forces users to automate the renewal process, which is good for everybody – certificates that are renewed every 90 days will be less likely to be affected by a vulnerability than a multi-year certificate that an admin isn’t actively renewing and updating as issues arise.
This leaves little reason to have an unsecured website or service in today’s internet. If you’re looking to host a webpage for your small business or personal site, seek out a web host that integrates free certificates into their service – many web hosts automatically support Let’s Encrypt nowadays. If you’re looking to secure another application, you may seek out a consulting firm like Avende to help determine whether an automated Let’s Encrypt certificate or a long-term TLS certificate is right for your application.

Recent Comments